Cyber security vendor FireEye recently disclosed that they were the target of a sophisticated attack that resulted in the loss of its array of offensive security tools. These OSTs were often used across FireEye technical service engagements to prove the value of their product stack.
Fireye Breached
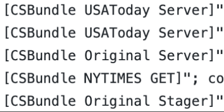
Some of the tools taken in this breach are based on well-known offensive frameworks, and the Cobalt Strike framework was definitely in use. This is evident in the naming convention used in the coverage by FireEye.
FireEye has also provided a list of CVEs to allow customers to identify any vulnerabilities these tools may be exposed to. However, it has been reported that none of the tools target zero-day vulnerabilities.
Detection and Visibility
Here at CyberOne, we continue to monitor and hunt for relevant indicators of compromise, not only related to this attack but also to any malicious activity that may be occurring. If there are parts of your network that have not been secured, we encourage you to close the gaps.
Visibility into your environment is key to identifying malicious activity. If you don’t know what’s running on your endpoints, how do you know what you're securing? Here at CyberOne our Cyber Defence Centre is powered by Sentinel One which ensures we know what’s happening on every endpoint at all times, this then feeds into MS Sentinel to correlate our EDR information with other devices on the network such as Firewalls, Active directory logs, to have a full understanding of your environment at all times. This data is then enriched with Threat Intelligence, Artificial Intelligence, and known IOCs to ensure your environment is always secure. On top of this, the SOC team is constantly developing new detection techniques and proactive threat hunting to search for things such as misconfigured devices, out-of-date software, and malicious processes.
CyberOne is Here to Help
Here at CyberOne, we are committed to helping you secure your environments. We are here, ready to help. Here are a few tips from our team:
- Deploy a SIEM and 24x7 SOC team to monitor and defend against breaches.
- Ensure that your AV/EDR solution covers all of your environment. It is also important to keep all software up to date. Although no zero-day exploits have been found, some can still be used against you if you have not patched the vulnerability.
- If you need help conducting risk assessments of your estate related to the FireEye breach or even securing unprotected devices, CyberOne is ready to help you deploy Sentinel One in minutes without any business downtime or restarts. Sentinel One will then give you a full insight into your endpoints and what is running on them.
- Search your environment for the offensive security tool hashes. These tools may be on your network, waiting to take control. Create a search on your environment for the following hashes to ensure you haven’t seen any of the OSTs!
Latest FireEye Indicators of Compromise (IOCs)
00f866a2d0eda84ed2488ead86bc8acaa3700b3f
049f5f5ec6e34d2e40e445c0bc188be420e287c6
066954007501c38187ffa0877b02013a4d4dc0ba
092cbf66bd6a548d7baf6f8b215c2a3483a2564c
0bbe8738281328778b4cf5404cc866ebedbe4ca1
0e0aede7d4f97f0d054733baba3c8313864e187f
0f923286d803aaade3bf28fdb923f6917ebb0b20
1049eb7d4ddfbc895848a3680fa332f0fec10def
218651ac5b575c3f9642c2e9a5928aa22fab8483
22109552d6af71d392de199e21ae272009db608a
23b1e73bf4cc07cd31b92a8c294b341740484d3e
23e93aa315f9a1268077131d68429055ac102b25
28a15a0b532c47110297aa6f4f46bad4d72235a2
2a5b9098d073406ecb3fffe8d6cba6b5ed26ce5a
32687a64efe5246f9b7284b5ae9adedc31605fdc
345da4a23cf56c22d218301ec461bfc3ca8e2cc2
390496bbd3f71d1ba08d7c86867d62b67597257d
43268f6f01a1aab72b62b63211ec1daef7ce34c0
46a6c17e1ec6d3aa4e931247c38a9219d71977a5
472af2b122c23bf0ca10c78d389a5a7f030a3536
5179d4d2fb102427e73ccd0cffa54a64405f41fb
562f4a310f37fafd5f66f460f79dc80912d2dad1
58cdc7d8e6175ef48d85a1b0602ed4024bf75019
599b70211175f44e7c651f0322cdc11084cc838e
5a69157821b615d11820036feb64d479009f6970
5adc9856172203858f5b93f67f4bf5814ad0df8a
5d358567e549a6f8e471697f7c78bc8bdf2a6534
5e6a5c287c9a8c412f1868b6f86bc23b75e1d1b9
6d44aa3772738143f26493caa6996dbdd1dcc048
7358ef9186c6fdf11016739496af19c5d3ecc193
73b98fd25755cd509ad5e4db4332ea18b651a0b5
780b6854d2d97834a068220e9060a874434161be
81ae80a486081e626a853d8759b37cdb36683f1a
82739c78f7b351bbe80a582fd46b0ba4f1c8c02b
8ae7c7830eb38b19c516df52db98b8abdb3df68d
8c58a1918f24473e55c7b239ca0f890f78fc17b9
8ec6fedc9ac60ee42ca93cc0aebfa55f572a1473
903de96e966183883ae1c1ccaa0d30e8684ad0d9
9577be0570e464af72f385479bae9ee9c2a082d4
9c21dc8726acd445b4defccfdecc14fad6e6ac78
9f595dc903e24c6a03ba95a701037b6532050667
a199a5b6584f1ce713753d1b2767d02f166948a4
aded10ffd74bc07e1aa622911389a31d3bee605a
b2d98ac491b2a60f29991bd858f62594b85ddcfb
b98cded462dfd80c682c953830e3df744cac756d
ba8f4a2c864ea2031f95c49c43dd7f1cc22d72f5
c1a031b4725cd740df986d29c3e94992813fccc8
c47021b5fc733b1a21e837fd34f849e0559b1ace
c7d1f8ad918ae32c5eee34ed4571775aa00cf3ad
c968672b966086fb9fa8b5e6b7124dec6a4119f3
cc542c0f873470b3eb292f082771eec61c16b3d7
cd3bb41346fdc37053dc6b5a83f2c77fe4e2c3bf
d04afd993d41fe68d31a7a9848d9ab31f7933991
d16c01db635b05a219ae8eef3728fae55adfcb4e
d535de08875cef1c49bfa2532281fa1254a8cb93
daedb9d53501dcb655044ce4cbb5d39a645070b4
e384c7371f681af5d4fc167f3f66bf68ac1f3bdb
e4fbc8961cb54d27d834f5789c7b4d1f4819fd34
e54f5737847287e49a306f312995c9aba38314d4
f590b00fd30a653a833be42974f9f714d3c8d595
f871d7a9fd37f2250db8658beb6b5ef6e794a08b
f9881d2380363cb7b3d316bbf2bde6c2d7089681
We’re here to help, we’re here to secure your environments.


