Cybercrime has reached a staggering milestone. If measured as an economy, it would rank as the third largest in the world, worth an estimated $9.2 trillion annually. Against this backdrop, the question for business leaders is no longer if they will face a cyber incident, but when.
At CyberOne’s recent webinar “Cyber Crisis: Are You Ready to Respond & Recover?”, experts shared their perspective on what it means to build true resilience in an era where attacks are constant, sophisticated and often business-ending.
Led by Charlie Morgan-Harris, with insights from Lewis Pack (Head of Cyber Defence) and Philip Ridley (Director of Cyber Risk Management), the discussion went beyond surface-level advice to deliver hard-earned lessons from the frontline.
The Cyber Readiness Gap
Despite the scale of the threat, readiness remains shockingly low. According to the UK Government’s Cyber Security Breaches Survey, only 22% of businesses maintain a formal incident response plan. For Ridley, this is less about oversight and more about the competing pressures facing leadership:
- Resource shortages: Cyber security still trails behind traditional IT in workforce capacity
- Budget tension: Only one-third of leaders cite security investment as a priority
- Misplaced optimism: Many still assume they are too small or too niche to be targeted
“It’s not a case of if they happen, it’s a case of when they happen.”
Philip Ridley, Director of Cyber Risk Management, CyberOne
Whether it is a global brand like Marks & Spencer, a healthcare trust or a regional manufacturer, the reality is the same: every organisation is a potential target.
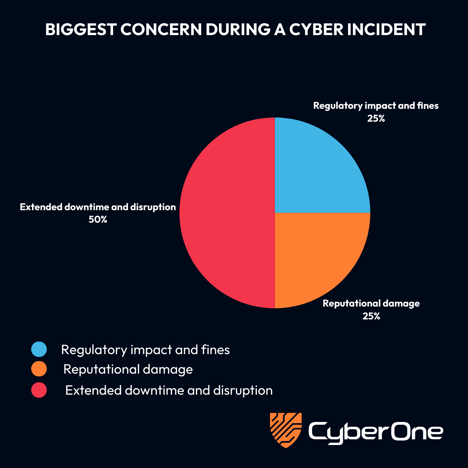
This was reflected in the live poll conducted during the webinar. When asked what would concern them most during a cyber incident, 25% said regulatory impact and fines, 25% said reputational damage. Still, the majority, 50%, cited extended downtime and disruption as their biggest fear.
Another poll revealed a preparedness gap. When asked how prepared they felt to respond to a major cyber incident today, 28.6% admitted they were not very confident, while 71.4% said they were somewhat prepared but recognised gaps.
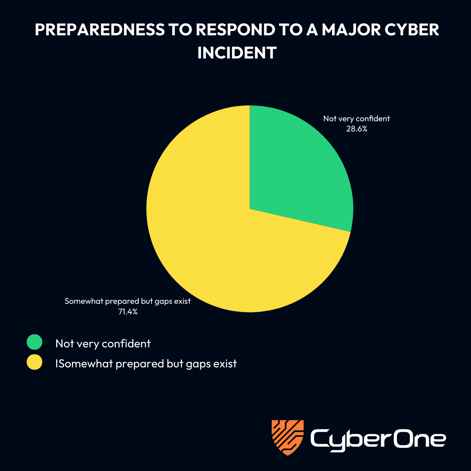
Together, these results underscore a sobering reality. Even engaged professionals attending a cyber crisis webinar acknowledge that resilience is not where it needs to be, and that downtime, disruption and uncertainty about readiness remain the most pressing concerns.
Why You’re a Target: The Threat Actor Ecosystem
The modern threat landscape is dominated by sophisticated ecosystems of nation-state actors, hacktivists, insider threats and criminal gangs.
“Everyone is a target. That’s a known fact.”
Lewis Pack, Head of Cyber Defence, CyberOne
The point is simple: everyone is valuable to someone. Whether as a stepping stone in a supply chain, a source of data or a political target, no organisation can safely claim immunity.
Incident Response: From Chaos to Coordination
Preparation is the bridge between a cyber crisis and business continuity. Yet, as Ridley highlighted, many organisations blur the lines between digital forensics (DF), which investigates the root cause, and incident response (IR), which provides the structured playbook for survival. Both are essential, but they serve different roles.
A live poll during the webinar showed how wide the gaps remain. When asked if their organisation had a formal incident response plan in place, 42.1% said yes but it needs updating, another 42.1% said yes fully documented and tested, and 15.8% admitted they have no plan yet but are working on one. The message is clear — even when plans exist, many are outdated or incomplete, which risks leaving teams uncoordinated when an incident unfolds.

“Spectacular achievement is always preceded by unspectacular preparation.”
Philip Ridley, Director of Cyber Risk Management, CyberOne
At its core, an IR plan prevents what Pack called “the headless chicken effect”, chaotic reactions that waste precious time and compound damage.
What Good DFIR Looks Like
Not all DFIR services are created equal. When selecting or evaluating a provider, there are several non-negotiable qualities that define good.
- 24/7 Availability
Attackers do not work 9–5. A capable DFIR partner like CyberOne must be able to mobilise immediately, around the clock. - Cross-Disciplinary Support
From legacy mainframes to cloud-native systems and operational technology, incidents rarely fit into neat technical boxes. Strong providers bring multi-domain expertise and partner connections. - Independent Validation
Look for accreditations such as NCSC and Crest, which prove capabilities are externally verified rather than just self-claimed. CyberOne holds both, along with multiple Microsoft certifications, reflecting a commitment to recognised industry standards. - Recovery Capability
Forensics and containment are only half the battle. A good DFIR service helps restore operations quickly by defining the organisation’s minimum viable company and guiding recovery to that state. - Strength in Depth
Providers should offer tiered expertise including security analysts, infrastructure engineers, PR advisors and legal counsel so incidents can be managed across every dimension. - Honesty About Scope
“If a provider tells you they can do everything, they are lying to you.”
Lewis Pack, Head of Cyber Defence, CyberOne
The strongest providers admit their limits and maintain trusted partner networks to cover specialist systems.
Practical Incident Survival Checklist
Drawing from years of live response experience, Pack outlined six survival rules that any business can adopt immediately.
- Prioritise containment above all else – Stop the spread first
- Ask for forgiveness, not permission – Act quickly to protect the business
- Define a single point of command – One decision-maker reduces confusion and delays
- Establish centralised communications (plus a backup) – Create a war room and plan for a fallback channel
- Document everything – Logs, screenshots, transcripts, insurers and regulators will expect proof
- Accept mistakes will happen – Speed and progress matter more than perfection
“Readiness defines resilience. The time to act is before, not after, the next attack.”
Lewis Pack, Head of Cyber Defence, CyberOne
For organisations without a formal plan, this checklist alone can mean the difference between recovery and catastrophe.
Live poll results from the webinar underscored this point. When asked if their organisation had a clear telephony verification policy for confirming sensitive information, 61% said yes and it is actively followed, while 16.7% said yes but not consistently used. Another 16.7% admitted they had no policy but recognised the need, and 5.6% said no and not a current priority. This reveals a worrying gap between awareness and disciplined execution, exactly the kind of weakness attackers exploit when attempting to bypass helpdesks or re-register MFA credentials.

Resilience Is a Continuous Practice
Resilience is not a set-and-forget exercise. Post-incident reviews, tabletop simulations and continuous updates to IR plans are essential.
A live poll during the webinar confirmed this challenge. When asked when their organisation last carried out a cyber security table-top exercise or simulation, 45% said within the last 6 months, 40% said 6–12 months ago, 10% said over 12 months ago and 5% admitted they had never run one at all. This means that more than half of organisations are either overdue or have never tested their response plans, leaving them exposed if a real incident occurs.
Building resilience requires businesses to ask hard questions:
- What is our minimum viable company in the face of a crisis
- Can we rebuild infrastructure quickly and safely
- Do we have a backup communication plan if our primary system is down
- Are we testing and refining our response regularly
As Ridley put it, failure is not an endpoint but a teacher: “Failure is just the opportunity to begin again.”
Why Preparation Today Protects Tomorrow
Cyber crises are not abstract threats; they are lived realities playing out daily across industries. The organisations that emerge stronger are not the ones with the biggest budgets but the ones with the clearest plans, the most disciplined preparation and the strongest partnerships.
Readiness defines resilience. The time to act is now.
Ready to take the next step?
CyberOne offers a free 30-minute one-to-one consultation with our specialists. We will review your current preparedness, highlight gaps and recommend practical next steps to strengthen your cyber resilience.


.png)