Most organisations approach data security as if it were 2015. They deploy multiple-point solutions whenever a new risk emerges, creating a patchwork of tools that don’t communicate. The result? Catastrophic blind spots that attackers exploit daily.
Data no longer lives in silos. Sensitive information flows across devices, emails, SharePoint repositories, Teams chats and third-party SaaS applications. Traditional fragmented security approaches cannot protect this reality.
These aren’t just statistics. They represent business-ending events for companies without unified data governance.
The Fragmented Security Trap
We see this pattern repeatedly at CyberOne, organisations build security strategies by adding tools reactively.
- One tool for endpoint DLP
- Another is for email scanning
- A third for cloud app discovery
- Spreadsheets to track access reviews
Each tool performs its narrow function adequately. However, the gaps between them create invisible vulnerabilities.
Consider The Following Scenario:
A professional services firm has deployed separate Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) solutions.
- The DLP monitored USB usage
- The CASB watched approved cloud apps
An employee copied a confidential client file to personal OneDrive for remote work. The endpoint DLP missed it because it wasn’t configured for cloud uploads. The CASB ignored it because personal accounts weren’t monitored.
|
CASB (Cloud Access Security Broker): A security tool (for example Microsoft Defender for Cloud Apps) that helps organisations monitor and control the use of cloud applications. It enforces policies for accessing approved apps and helps prevent data leaks to unapproved or personal cloud accounts. DLP (Data Loss Prevention): A security solution (for example Microsoft Purview Data Loss Prevention) that monitors and protects sensitive data from being accidentally or intentionally shared outside the organisation. It can block copying to USB drives, sending confidential emails externally or uploading sensitive files to unapproved locations. |
By the time IT discovered the breach through client notification, sensitive data was beyond corporate control. Breach notifications, potential fines and reputational damage followed.
This exemplifies fragmented security failure, each tool succeeded in its silo, while the organisation failed catastrophically.
Shadow Data: The Invisible Killer
Shadow Data refers to sensitive information that exists outside of your approved or monitored systems.
- It includes files saved to personal cloud accounts, unmanaged devices or unapproved apps
- It often arises when employees work around official processes to get things done more quickly
- Because it isn’t visible to traditional security tools, it creates serious blind spots that attackers can exploit
- One in three data breaches in 2024 involved shadow data outside of centralised management.
Point solutions cannot protect what they cannot see, modern data sprawl creates massive blind spots that traditional tools miss entirely. Microsoft Purview represents a fundamental shift from this fragmented chaos to unified data governance.
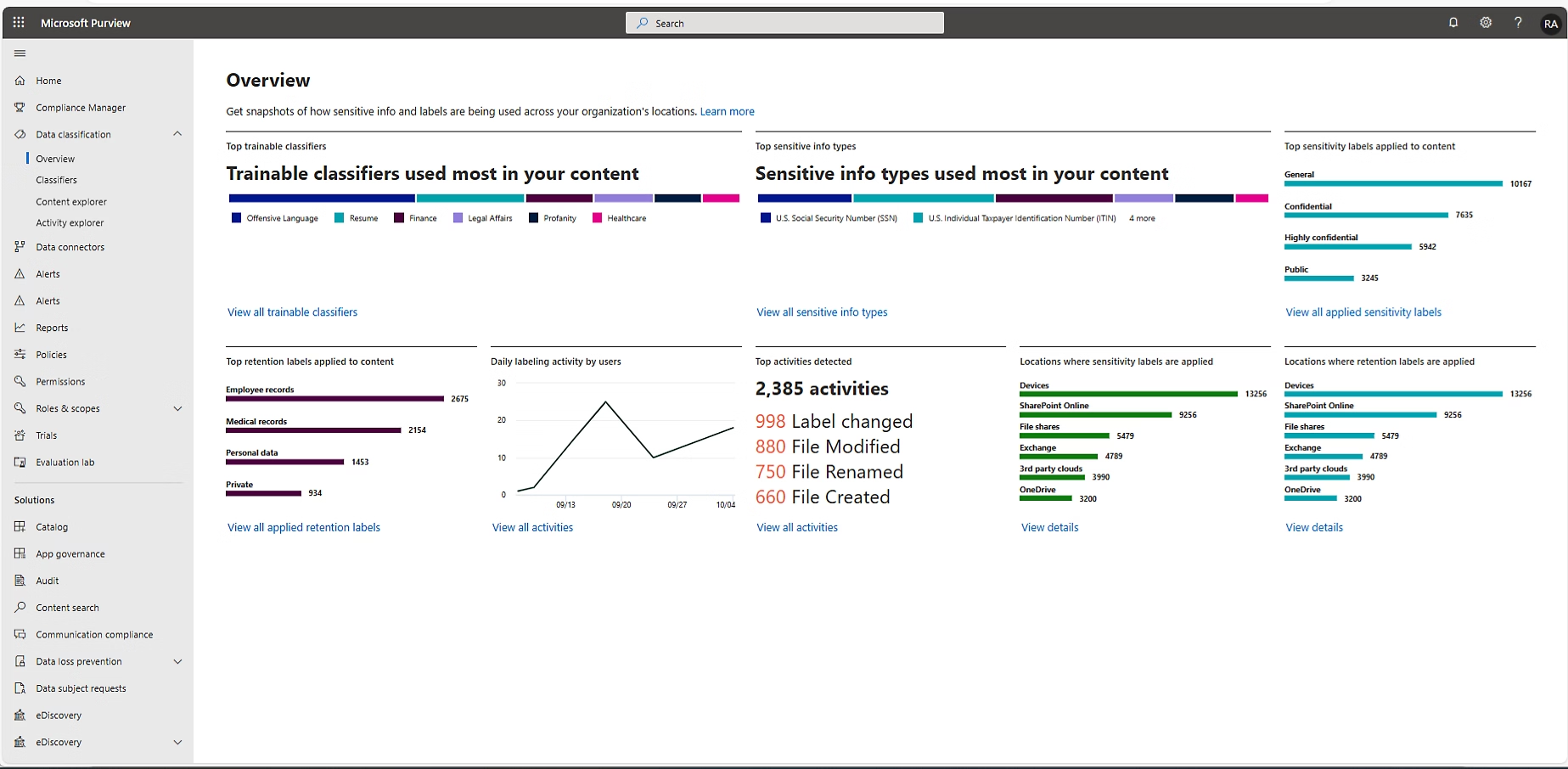
What Is Microsoft Purview?
Microsoft Purview is a unified Data Security, Governance and Management tool with the below benefits:
- One Place to See & Manage All Your Sensitive Data - Instead of multiple separate tools, Purview provides a single dashboard to discover, classify and protect data wherever it resides.
- Automatically Finds & Labels Sensitive Data - Purview scans emails, documents, SharePoint, OneDrive, Teams and non-Microsoft systems to identify sensitive information, such as credit card details or personal information.
- Consistent Data Protection Everywhere - Security policies you set in Microsoft Purview apply automatically on devices, in the cloud, in email or when sharing files.
- Stops Data From Leaking Accidentally - For example, it can block the sharing of confidential files to personal accounts or unapproved apps.
- It Makes Compliance Easier - Purview helps you meet rules like GDPR by showing what data you have, where it is and who can access it.
- Works With AI-Generated Content - Purview’s labels and policies also cover data created by Microsoft’s AI tools, ensuring security keeps pace as your business utilises AI.
The Unified Framework Advantage
Microsoft Purview delivers what fragmented tools cannot: end-to-end visibility and control across your entire data estate. Instead of managing separate tools that don’t communicate, you define policies once and apply them everywhere data lives.
A document labelled “Confidential Client Data” stays protected whether it’s on a laptop, emailed or uploaded to the cloud. Sharing personal accounts is automatically blocked. You receive consistent monitoring and alerts through a single dashboard.
This unified approach eliminates the gaps between security checkpoints that attackers exploit.
Starting With Discovery, Not Deployment
Most organisations struggle with a fundamental challenge: they don’t know what sensitive data they have or where it lives.
You cannot protect what you cannot see and you cannot govern what you cannot classify.
The first step toward unified data governance is discovery, Microsoft Purview’s automated scanning and classification capabilities handle this heavy lifting.
Purview scans your environment across SharePoint, OneDrive, Teams, Exchange, on-premises data stores and integrated non-Microsoft cloud applications. It identifies sensitive data locations even when you didn’t know they existed.
Built-in sensitive information types automatically classify credit card numbers, GDPR personal data and custom patterns you define. You don’t manually tag every document.
The central dashboard displays the data you have, its location, access methods and the users with permissions. This visibility alone transforms most businesses’ security posture.
The Human Element: Managing Change
Technology deployment is straightforward. Change management is the real challenge. Teams that have been operating with fragmented tools for years naturally resist unified approaches. A response we often hear is “our current system works fine”. We address this human element through stakeholder engagement and a phased adoption approach.
- We acknowledge what’s working while highlighting what is missing. We don’t declare existing systems broken. Instead, we identify blind spots and manual efforts that create risk.
- We focus on business outcomes everyone cares about: protecting customer data, avoiding compliance fines, preventing reputational damage and reducing operational overhead.
- We emphasise minimal disruption through phased implementation. Start with discovery and visibility without blocking rules. Gradually classify and label data. Roll out policies in monitor mode first. Only enforce blocking once the impact is understood.
This approach respects existing workflows while incrementally improving security.
Measuring Success: Performance-Led Implementation
Success isn’t measured by the features deployed, but by the outcomes delivered and we focus on business-relevant metrics that prove value.
Data discovery coverage indicates the extent to which your data estate becomes transparent and accessible. Classification adoption tracks the percentage of data correctly labelled under policies like “Confidential” or “Regulated Data.”
Policy coverage demonstrates consistent control deployment across endpoints, email, Teams and SharePoint. Incident reduction metrics indicate a decrease in risky events over time.
Compliance posture improvements provide audit-ready reporting for GDPR, ISO27001 and other frameworks. Operational efficiency gains are highlighted by the elimination of redundant tools and a reduction in manual investigation time.
These metrics transform Microsoft Purview from an IT project into a strategic business enabler, delivering greater visibility, consistent protection, reduced risk, easier compliance and lower costs.
Prioritising Implementation: Business Risk First
Organisations face resource constraints that demand ruthless prioritisation, we never recommend protecting everything equally. That approach protects nothing well.
Instead, we start with a business risk assessment, what data would hurt your business most if it leaked, was stolen or became unavailable?
Client contracts, financial records, intellectual property, customer PII or regulated data under GDPR represent typical high-value targets.
Stakeholder workshops involving business owners, compliance leads and executive sponsors map critical data priorities. This builds buy-in while ensuring protection focuses on what matters to the organisation.
Microsoft Purview’s automated scanning capabilities quickly answer where priority data lives across SharePoint sites, OneDrive folders, Exchange mailboxes and Teams channels.
We configure sensitivity labels and policies to automatically identify high-value data, starting in monitor mode to observe real-world usage without disrupting workflows.

This evidence-based approach enables targeted protection policies—blocking external sharing for truly sensitive labels, requiring encryption for regulated data types and alerting on unusual access patterns.
Future-Proofing for the AI Era
AI fundamentally reshapes data security requirements. Microsoft Purview usage has skyrocketed over 400% since its launch, reflecting the urgent market recognition of this reality.
AI creates a double-edged sword for data security. It accelerates productivity through content generation, data analysis and process automation. However, it exposes risk surfaces through sensitive data flowing into public AI tools, AI models generating confidential summaries and increased data sprawl resulting from SaaS AI integrations.
Data moves more freely and gets transformed in ways traditional policies never anticipated.
Microsoft Purview addresses this challenge through AI-powered discovery and classification that automatically detects sensitive data, even when it is newly created, renamed or moved. Consistent policy enforcement across Microsoft 365, Azure and third-party clouds ensures unified rules follow data through AI-driven workflows.
Sensitivity labelling and governance are built into Microsoft’s AI tools, such as Copilot, meaning your governance model evolves to cover AI-generated content alongside human-created data.
The Strategic Imperative
Unified data governance with Microsoft Purview isn’t an IT expense, it’s how you protect your reputation, build customer trust and enable growth without fear.
Your data is your business. Client contracts, pricing models, IP, employee records and regulated customer data represent your most valuable assets.
When that data leaks, gets stolen or is misused, the consequences extend far beyond IT. Lost customers, damaged reputations, regulatory fines and lawsuits threaten the survival of businesses.
Unified data governance provides control and confidence:
- You know where sensitive data lives
- You ensure consistent protection everywhere
- You reduce breach and compliance failure risks
- You demonstrate to clients and regulators that security is a priority
This transforms security from a fragmented, reactive cost centre into a proactive business enabler that supports growth, technology adoption and workforce empowerment without compromising your most valuable assets.
Taking Action This Week
Organisations convinced of the need for unified data governance but overwhelmed by implementation complexity should start with a single, straightforward action.
Get key stakeholders in one room and answer this question together: “If this data got out, what would genuinely hurt us?”
That single conversation becomes your starting point:
- You don’t need to make a purchase yet
- You don’t need comprehensive policies or perfect data estate knowledge
- You need clarity on what truly matters.
Unified data governance succeeds or fails in prioritisation, trying to protect everything equally means protecting nothing well.
By agreeing on the highest-value, highest-risk data types this week, you’ll achieve clear alignment between IT, compliance and business owners. You’ll have a targeted, realistic first scope for Microsoft Purview deployment. You’ll build a powerful business case for leadership that focuses on protecting what truly matters.
The fragmented security approach that was effective in 2015 now creates catastrophic vulnerabilities. Microsoft Purview offers the unified framework that modern data realities demand.
Practical Next Steps
- Map Your Current Tools: List all the data security tools you use today and identify where they don’t talk to each other.
- Identify Your Critical Data: Agree internally on the types of data that, if leaked or lost, would cause the most damage.
- Run a Discovery Workshop: Bring IT, compliance and business leaders together to review where your sensitive data is stored and how it is moved.
- Evaluate Microsoft Purview Fit: Use the insights above to decide if Purview can unify your policies, reduce manual effort and close gaps.
- Plan a Proof of Concept: Consider a small-scale Purview implementation in monitor mode to prove value without disrupting current workflows.
- Build Your Business Case: Utilise outcomes from the pilot, such as improved visibility, reduced incident rates and simplified compliance, to justify broader adoption.
Ready to Move from Fragmented to Unified Data Security?
Your Data Is Growing Fast—Is Your Security Keeping Up?
Join us on Thursday 25th September 2025 10:00 (UK time) for our webinar: Discover how Microsoft Purview delivers end-to-end visibility, consistent protection and simplified compliance, turning security from a cost centre into a strategic business enabler.
How Could This Work For Your Organisation?
You may qualify for a Microsoft-funded Data Security Engagement to map your sensitive data and design a unified governance strategy.
Find Out More & Check Your Eligibility
Want Expert Help to Get Started?
Learn more about CyberOne's Microsoft Purview powered Data Security as a Service and how we can manage it 24x7 for you.



